29 Jun Improving Cyber Security
- Anirban Dasgupta
TWT Pune took an initiative for all tech writers, researchers, and subject matter experts to participate in a Pan India Whitepaper contest on April, 2023. Among several participants, Anirban Dasgupta emerged as the second Runners-up.
In the current age of Cyber Attacks, Cyber Security is of utmost importance for Information Technology (IT) companies across the world.
Introduction
In the current age of Cyber Attacks, Cyber Security is of utmost importance for Information Technology (IT) companies across the world. IT companies worldwide spend billions of dollars on protecting and securing IT assets from Cyber Attacks. Nowadays, IT companies have added “Security” as part of every phase involved in the Software Development Life Cycle (SDLC). Hence SDLC has now evolved as Secure Software Development Life Cycle (SSDLC).
Whatever a computer or an electronic device is connected to the network over the internet, it is prone to malicious attacks by cyber criminals. Cyber Security is the broad term which involves protecting computers systems, mobiles, electronic devices, servers, networks etc from such attacks over the internet. Cyber Security ensures authenticity of data, integrity in its original form, confidentiality, availability and non-repudiation which validity the legitimacy of the data. Cyber Security can be applied as Application Security, Network Security, Cloud Security, Mobile Security, Internet of Things (IOT) Security, Data Center Security, Endpoint Security etc.
Identity Access and Management (IAM) is a Cyber Security technique which is employed for user management and access permissions to a device or computer system over the internet. It is mostly used in providing Cloud or Network Security. IAM provides features like Single sign-on (SSO), Multi-factor Authentication (MFA) and Adaptive Authentication. IAM is the core of Zero Trust Architecture (ZTA) and is the most widely used and adopted technique across the globe.
Zero Trust Architecture ensures that irrespective of whether the electronic device or computer system is inside the company network or outside it, every access request from any user to it or any of its applications must be validated for its authenticity. Hence only legitimate users are allowed access to such ZTA based systems. In other words, ZTA stands for “trust but verify” which means even for already trusted devices or computer systems, revalidation of trust is a must. ZTA prevents Cyber Attacks as the intruders must constantly validate their identity for gaining access to each resource on the network. ZTA uses various analytics techniques and hence an illegitimate intruder access is denied. Hence ZTA provides a comprehensive Cyber Security solution for users, applications and infrastructure for an enterprise.

Architecture of Zero Trust Framework
The actual ZTA architecture varies from companies to companies based upon their own implementation and deployment. However, the basic logical architecture remains similar for most of the enterprise ZTA solutions. There are multiple logical components involved in the ZTA which work in close coordination. The ZTA logical components are deployed as a web service either on-premises or on the Cloud.
Just like any Network Application, there is a control plane which consists of the Policy Decision Point (PDP) and the communication interface for interaction between logical components of the ZTA. The PDP is segregated logically into Policy Engine (PE) and the Policy Administrator (PA). The data place is used for communication between application data
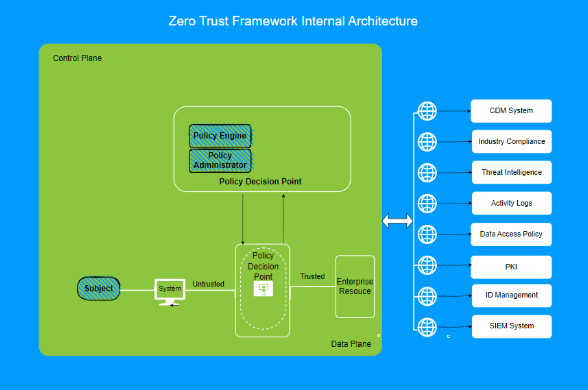
As per the diagram, the core components of ZTA are as follows:
- Policy Engine (PE): This uses the corporate enterprise policy to make a decision where to grant access to a resource for a given subject or user or not. It can grant, deny or even revoke access to a resource. The PE makes and logs the decision. It is tightly coupled with Policy Administrator (PA).
- Policy Administrator (PA): Once the decision is made by the PE, PA is responsible for executing the same and creating or shutting down the communication channel between the subject and the resource. It also takes care of the authentication mechanism.
- Policy Enforcement Point (PEP): Once the PA authorizes and authenticates a session between the subject and the resource, the PDP starts the actual session. However, if the session is denied by the PA, then PA instructs PDP to terminate the connection.
Other than the core components mentioned above, there are other data sources which provide input and policy rules. They are as follows:
- Continuous Diagnostics and Mitigation System (CDM): This is basically used as a diagnostics tool to monitor the state of the subject making the request whether it is up-to-date with the required software, updates etc.
- Industry Compliance System: This tool is used for enterprise compliance on the policy rules and whether they are adhered to.
- Thread Intelligence Feed(s): This tool is fed information from internal and external sources on the newly discovered vulnerabilities and threats.
- Network and System Activity Logs: This tool combines the network traffic, asset logs, resource access response and provides real time feedback on the enterprise security of computer systems.
- Data Access Policies: This tool provides policies and attributes for data access for the resources on an enterprise network.
- Enterprise Public Key Infrastructure (PKI): This tool is liable for creating and logging enterprise issued PKI certificates to the resources, subjects, services and applications.
- ID Management System: This tool is responsible for generating, storing and managing the user accounts and identity records for the enterprise.
- Security Information and Event Management (SIEM) System: This tool collects and stores security related information from the enterprise network which can be analysed later. This inference data available from the SIEM can be used to refine enterprise policies and warn of possible threats or attacks on the enterprise resources.
Advantages of Zero Trust Architecture
The benefits of ZTA are as follows:
- Increased and Improved Security: The “trust but verify” model definitely improves security in the enterprise network and deters Cyber Attacks.
- Greater Administrative Control: As discussed above in the ZTA architecture, the core ZTA components like PE, PA and PEP ensure greater administrative control in the enterprise network.
- Improved Compliance: The Industry Compliance System tool of the ZTA ensures greater compliance is adhered to for the enterprise policy rules.
- Greater Visibility: The real time information feed on policy activity provides a greater visibility to the enterprise policy administrators.
- Greater Efficiency: The ZTA is based on the IAM model and allows greater automation of enterprise networks without much manual intervention required. Hence it is definitely an efficient enterprise model.
- Lesser Risk Mitigation: By default, user access to all enterprise resources is set to “deny” and only the user who is authorized during each resource access request is allowed to access the enterprise network. Hence there is reduced risk for cyber criminals to break into the system.
Disadvantages of Zero Trust Architecture
Though ZTA has lot of benefits, there are some disadvantages which are as follows:
- Complex to Implement: ZTA architecture and its deployment is complex and it is not easy for enterprises to implement their own ZTA architecture and deploy it. For enterprises which don’t have one of its own ZTA deployment, they need to depend on third party vendors to deploy their ZTA systems on their enterprise network.
- Sandbox Applications: The ZTA architecture requires enterprises to maintain sandboxed applications for all IT assets. This will require each enterprise sandboxed application to be secure, which requires additional effort and expenses for the enterprises.
- Expensive: ZTA architecture is not just complex and expensive to implement, it also requires additional manpower to manage the ZTA system.
- Downtime and Productivity Issues: The biggest disadvantage users of ZTA network face is downtime of ZTA applications. This really affects productivity on the work front as all ZTA services are web-based applications.
Conclusion
During the Covid period, most of the IT organizations chose the work-from-home model. And presently the hybrid model is adopted. The ZTA Framework is widely used by such organisation to support such models for remote access to company resources. ZTA Network completely takes care of security access of company resources on public networks or ones outside the organization. This provides peace of mind for organizations who promote the work-from-anywhere model. ZTA also allows secure access to its IT resources within the company premises. Hence ZTA Model is most widely adopted and used across the enterprise organizations and it has gained tremendous traction over the few years. It is bound to grow leaps and bounds in the near future and may become a mandatory feature across the enterprise organizations.
About the Author
Anirban Dasgupta is a Software Development professional with 17+ years experience on C/C++/Golang on Networking and Security domains. He is currently working with Dell Technologies, Bengaluru as a Software Principal Engineer. His current work involves a multitude of roles like Individual Contributor, Project Lead, Product Owner, Agile Practitioner and Security and Vulnerability Champion. In his free time, he likes to play chess/carrom with family or listen to music.
Current Role: Software Principal Engineer
Company: Dell Technologies
City: Bengaluru
Connect at LinkedIn

“Security used to be an inconvenience sometimes, but now it’s a necessity all the time.”
- Martina Navratilova




No Comments